- Home
- Services
- Hi-Line Engineering
- About
- Careers
- Contact
- Requests For Proposals
What does the ransomeware attack on Colonial pipeline mean for the future of critical infastructure protection?
by GDS Associates, Inc | July 16, 2021 | Newsletter - TransActions , Cyber Security
 On May 7th, Colonial Pipeline was forced to shut down operations as a result of a ransomware attack. The shutdown lasted until May 12th and the effects of the shutdown were felt long after. Colonial Pipeline supplies 2.5 million barrels of fuel daily to the southeastern US. This accounts for about 45% of the fuel for the region and resulted in massive fuel shortages which lasted for weeks.
On May 7th, Colonial Pipeline was forced to shut down operations as a result of a ransomware attack. The shutdown lasted until May 12th and the effects of the shutdown were felt long after. Colonial Pipeline supplies 2.5 million barrels of fuel daily to the southeastern US. This accounts for about 45% of the fuel for the region and resulted in massive fuel shortages which lasted for weeks.
The gas industry, as well as others who are part of the critical infrastructure, are extremely vulnerable to cyberattacks. Many of the different industries that make up the critical infrastructure do not have any regulations in place to protect against these kinds of attacks. The attack on Colonial Pipeline was not even trying to disrupt pipeline operations. The group that targeted Colonial Pipeline saw them as an easy target, and just wanted to make money. However, Colonial Pipeline did not have their operations network properly segregated from their business network and an attack on the business network resulted in a complete shutdown of their operations network.
Many critical infrastructure industries, including the natural gas industry, do not have the same regulations as the electric power
industry. The electric power industry has an entire set of cybersecurity standards, the NERC (North American Electric Reliability Corporation) CIP (Critical Infrastructure Protection) Standards, that they must follow in order to prevent this type of occurrence. These standards exist today as a result of the 2003 northeast blackout, which left over 55 million people without power. It is only a matter of time before similar measures are going to be put in place across all industries that make up our critical infrastructure.
Natural gas and electricity go hand in hand and if something effects the gas supply, it will also affect electricity generation. The February 2021 events that unfolded in the South-Central region of the United States were caused by cold weather and drastically affected the ability of natural gas suppliers and pipelines to deliver gas to electric generation. But if a cyberattack were to impact the gas pipelines in the same way, that in turn would similarly cascade into additional critical infrastructure, such as the electric grid. If we want to protect our electric grid, then it makes sense to protect our gas pipelines as
well since these systems do not work in isolation and are all co-dependent.
- Improve threat information sharing between government and private sector
- Increase and improve cybersecurity standards in the Federal Government
- Improve supply chain security
- Create a cyber safety review board
- Create a standardized process for responding to cyber security incidents
- Improve measures for detecting and mitigating potential threats
From this executive order, we can see that the increase in
recent cyberattacks warrants additional measures to be taken in cybersecurity, specifically surrounding supply chain and incident response. This is the second time President Biden is addressing supply chain, following the previous executive order signed on February 24th. NERC’s most recent additions to the CIP Standards included adding in a Supply Chain Risk Management Standard and improving the current Incident Response Standard. Additional agencies within the Federal Government are also starting to see an increase in cybersecurity regulations.
The executive order targeting supply chains calls for two separate reviews of supply chain vulnerabilities. The first, targeting vulnerabilities related to semiconductors, batteries, strategic minerals, and pharmaceuticals. The second, targeting vulnerabilities in critical sectors, including defense, public health, information technology, energy, transportation, and agriculture. The goal is to eventually limit reliance on products from competitor nations.
Over the past few years, the world has seen a dramatic increase in both cyberattacks and more specifically, ransomware attacks. Just recently, Kaseya, an information technology firm, was hit by a ransomware attack. This single attack has affected around 800 to 1,500 businesses around the world. Back in 2020, SolarWinds, an information technology and software development firm, was also hit with a major cyberattack. This attack affected around 18,000 SolarWinds customers, including the US Department of
Homeland Security.
The US was hit with over 65,000 ransomware attacks in 2020, and that number is only expected to continue rising. The rise in
popularity of Bitcoin and other cryptocurrencies is also making it easier for attackers to demand and receive ransom payments outside of the traditional financial institutions. Colonial Pipeline paid its attackers around $4.4 million in order to get their systems back under their operational control. The group behind the Colonial Pipeline cyberattack, Darkside, specifically targets hospitals, schools, non-profits, and governments. They are not alone, these targets typically have less cybersecurity protections in place, have neglected IT staff and infrastructure, and can afford to pay out larger sums in order to regain control of their systems.
The continued proliferation of ransomware attacks will hopefully push other industries classified as critical infrastructure protection to implement cybersecurity regulations. The NERC CIP Standards, which were developed for use to regulate the electric power industry were based around the NIST SP 800 series. NIST is the National Institute of Standards and Technology. It is a physical sciences laboratory and a non-regulatory agency of the United States Department of Commerce. For entities looking to increase their cybersecurity protections, this is a great place to look for guidance. Specifically, the NIST SP 800-53 Security and Privacy Controls for Information Systems and Organizations, provides a good baseline catalogue of security and privacy controls to follow.
NIST SP 800-53 was originally created in order to help improve the security of the information systems used within the federal government but has since been expanded to include non-federal information systems. The controls are broken up into low, medium, or high classes based on impact level. These controls are placed in 20 different families within cybersecurity. The control families include:
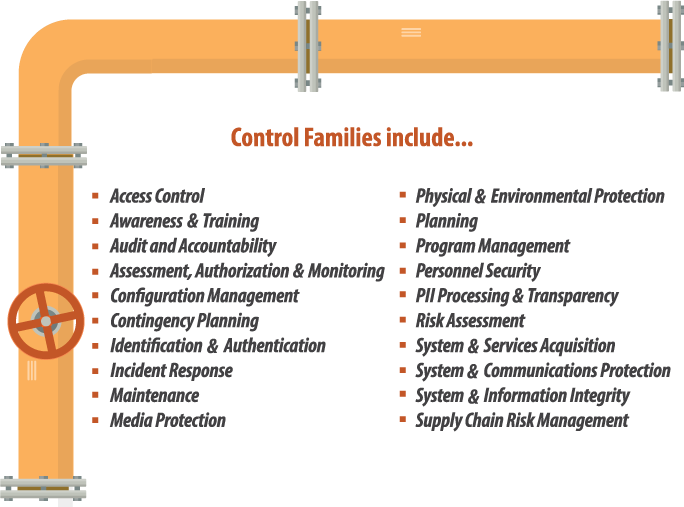
Implementing even the low impact controls across all of the control families will drastically improve cybersecurity protections.
Another great resource for preventing these kinds of attacks isGridSecCon. GridSecCon is an event put on by NERC every year to help entities with their incident response and recovery procedures. They put on a simulated widescale event that emulates a cybersecurity attack against the critical infrastructure in the US. Entities are supposed to coordinate and work together with one another, working through their individual incident response processes and eventually recover from the simulated event. This event started out as a tool for electric utilities to better know their incident response procedures, but has since expanded into a more widescale event that encompasses more critical infrastructure and also includes the addition of gas industry participants.
 Some commonsense activities also include:
Some commonsense activities also include:- Spending additional funds on IT and Cybersecurity infrastructure, systems, and incident response training
- Providing protocols for the company’s IT and operations staff to work together on cybersecurity related problems and solutions
- Ensuring the company’s business networks and operations networks are properly separated
- Develop a cybersecurity program (if you do not already one) or look for areas of improvement within the existing cybersecurity program.
James Fenstermaker is the Cyber Security Lead Project Consultant at GDS Associates. He works with Clients throughout the United States to develop and assess their cyber security programs and practices.
For more information or to comment on this article, please contact:
James Fenstermaker, Project Consultant |CONTACT
GDS Associates, Inc. – Marietta, GA
770-799-2480 or james.fenstermaker@gdsassociates.com
GET OUR NEWSLETTER
RECENT POSTS
- Protect the Grid: Act on Facility Ratings Today
- Why MOD-026-2 Matters: Raising the Bar for Generator and IBR Modeling Reliability
- Exploring the 2026-2028 Reliability Standards Development Plan
- Blackstart Resource Availability During Extreme Cold Weather Conditions
- DOE Pushes FERC to Accelerate Large Load Grid Access
Archives
- December 2015 (8)
- June 2025 (7)
- January 2016 (6)
- July 2016 (6)
- March 2021 (6)
- May 2022 (6)
- August 2020 (5)
- March 2015 (4)
- January 2019 (4)
- June 2019 (4)
- August 2019 (4)
- February 2020 (4)
- May 2020 (4)
- June 2020 (4)
- December 2020 (4)
- July 2021 (4)
- October 2021 (4)
- April 2024 (4)
- December 2024 (4)
- May 2025 (4)
- April 2015 (3)
- August 2016 (3)
- February 2017 (3)
- July 2017 (3)
- February 2018 (3)
- February 2019 (3)
- November 2019 (3)
- March 2020 (3)
- April 2020 (3)
- September 2021 (3)
- December 2021 (3)
- August 2022 (3)
- December 2022 (3)
- April 2023 (3)
- July 2023 (3)
- December 2023 (3)
- September 2024 (3)
- October 2025 (3)
- December 2025 (3)
- May 2014 (2)
- February 2016 (2)
- March 2016 (2)
- September 2016 (2)
- November 2016 (2)
- January 2017 (2)
- July 2018 (2)
- November 2018 (2)
- March 2019 (2)
- May 2019 (2)
- July 2020 (2)
- September 2020 (2)
- April 2021 (2)
- August 2021 (2)
- October 2024 (2)
- September 2025 (2)
- February 2014 (1)
- April 2014 (1)
- July 2014 (1)
- August 2014 (1)
- November 2014 (1)
- February 2015 (1)
- May 2015 (1)
- June 2015 (1)
- November 2015 (1)
- October 2016 (1)
- December 2016 (1)
- October 2018 (1)
- December 2018 (1)
- April 2019 (1)
- July 2019 (1)
- September 2019 (1)
- October 2020 (1)
- November 2020 (1)
- February 2021 (1)
- April 2022 (1)
- July 2022 (1)
- October 2022 (1)
- August 2023 (1)
- October 2023 (1)
- July 2025 (1)
- November 2025 (1)
- January 2026 (1)
Categories
- Newsletter - TransActions (85)
- News (78)
- Employee Spotlight (35)
- Energy Use & Efficiency (28)
- Energy, Reliability, and Security (18)
- Other Specialized Services (11)
- Environment & Safety (10)
- Power Supply (8)
- Transmission (8)
- NERC (7)
- Utility Rates (7)
- Cyber Security (5)
- Energy Supply (4)
- Hi-Line: Utility Distribution Services (4)
- Battery Energy Storage (3)
- Uncategorized (2)
- Agriculture (1)
- Hi-Line: Seminars & Testing (1)