- Home
- Services
- Hi-Line Engineering
- About
- Careers
- Contact
- Requests For Proposals
Securing Critical Utility Functions Effectively & Efficiently
by GDS Associates, Inc | February 16, 2018 | Newsletter - TransActions
 As we have seen through recent cyber-attacks, even the most secured cyber systems may be vulnerable to hackers, foreign actors, or other persons with malicious intent. In 2016, a major attack occurred using devices that were part of the Internet of Things (IOT), to block access to critical applications that rely on internet connections. This exposed even the simplest internet facing devices, such as smart TVs, appliances, and cameras. They can be controlled and used for malicious purposes, and typically have very little protections. It is more important now, more than ever, that we protect are critical assets. Electric utilities are one of the most critical components of our national infrastructure, yet some of the devices used to control the electric system are left exposed and do not have adequate cyber security protections in place to deter malicious actors. Additionally, electric utilities have a wealth of customer information stored on their corporate systems, that could potentially be stolen. This could result in, at best, loss of trust from customer, and at worst, customers being exposed to fraud or identity theft. It is imperative that we, as electric utilities, work to protect both our Operations Technology (OT) (e.g. SCADA and Metering Systems), and our Information Technology (IT) (e.g. customer information and internal/confidential documents).
As we have seen through recent cyber-attacks, even the most secured cyber systems may be vulnerable to hackers, foreign actors, or other persons with malicious intent. In 2016, a major attack occurred using devices that were part of the Internet of Things (IOT), to block access to critical applications that rely on internet connections. This exposed even the simplest internet facing devices, such as smart TVs, appliances, and cameras. They can be controlled and used for malicious purposes, and typically have very little protections. It is more important now, more than ever, that we protect are critical assets. Electric utilities are one of the most critical components of our national infrastructure, yet some of the devices used to control the electric system are left exposed and do not have adequate cyber security protections in place to deter malicious actors. Additionally, electric utilities have a wealth of customer information stored on their corporate systems, that could potentially be stolen. This could result in, at best, loss of trust from customer, and at worst, customers being exposed to fraud or identity theft. It is imperative that we, as electric utilities, work to protect both our Operations Technology (OT) (e.g. SCADA and Metering Systems), and our Information Technology (IT) (e.g. customer information and internal/confidential documents).
Prior to the mandatory and enforceable date of the North American Electric Reliability Corporation (NERC) Reliability Standards in 2007, NERC and its predecessor the North American Electric Reliability Council, have set a focus on cyber security for the electric system. The Critical Infrastructure Protection (CIP) Standards focus on how electric utilities that are part of the Bulk Electric System (BES) need to protect those cyber systems that monitor and control the high voltage and bulk electric system. While these Standards and Requirements are only enforceable on entities that are part of the BES (entities that own looped transmission connected at 100 kV and above and/or generation facilities that have a rating of over 75 MVA), this can also be used as a best practice for securing any OT cyber system, and it can also be extended to other IT systems.

Training and Awareness are key components in securing both IT and OT systems. Many IT and OT security risks can be addressed through training and re-enforcement of good security practices. Often times, people will be the biggest threat to cyber security, so maintaining a culture of good cyber security awareness practices can be an excellent way to help reduce risk. Outside of the electric industry, Cyber Security Awareness has transformed into a major national initiative. As an example, the United States Department of Homeland Security (DHS) established October as “National Cyber Security Awareness Month”.
Cyber Security Awareness should be a corporate wide initiative and not just limited to the IT and OT personnel. Cyber Security Awareness Topics can include how to use complex passwords, looking out for phishing emails, and knowing how to report any suspicious activity to a supervisor or the IT/OT Team. The awareness material that is used for general staff members can be as simple as a poster that reminds them to keep their passwords secret, or a periodic e-mail reminding staff to only open attachments from known senders. It is just important to get in the habit of thinking about security. A best practice is to change out the Cyber Security Awareness material at least once a calendar quarter to keep the topic fresh and in the minds of the staff.
For IT and OT personnel, simple awareness material may not be sufficient to educate them on their roles
in protecting the critical cyber systems. These individuals would need training on how to protect the cyber assets that are critical to the operations of the electric system. The National Institute of Standards and Technology (NIST) developed a publication on how to design an information security awareness and training program, NIST Special Publication 800-50. This NIST publication is a good place to start when designing the training program for your IT and OT personnel. It is important to design a training program that meets the needs of the electric utility, and is not overly prescriptive or burdensome on the IT and OT staff. These training courses can be combined, since many of the topics that need to be covered will be the same in an IT and OT environment.
OT Systems and IT Systems differ fundamentally in the way they are designed. The primary function of an OT System is to monitor and control the electric grid, not secure it. Many of the OT configurations that are in use across the system were not designed with security in mind. This is associated with the electromechanical systems that were in use when these OT configurations were brought in. Now, with the systems becoming more interconnected, electronic security becomes an issue that needs to be in the spotlight.

Another difference between the two systems is the up-time requirements. OT systems need to be running 24/7/365, and in some cases, need redundant back-up systems in case of a failure. Transmission substations (100 kV and above) typically have both primary and back-up transmission Protection Systems, in case one fails. IT environments may also have back-up systems, but it is not as critical to have zero down time for an IT system. Control Center OT systems also need to have an extremely high availability with little to no down time, so that the utility does not loose visibility of their electric system. When compared to a Control Center OT system, the IT system may not be as critical to the overall operations of the electric utility. For these reasons, it is important to jointly train and educate your IT and OT staff on which systems are the most critical to operations of the utility, and the dangers of taking down the OT system without a hot back-up option available.
Now, the technologies and hardware used in IT are becoming much more prevalent in OT Systems. Entities want to have the monitoring and controlling capabilities that come with an integrated system. With that approach comes additional security risks that entities are going to need to be made aware. It is estimated that about 80% of security issues faced by OT are almost identical to IT, while about 20% are unique to the OT infrastructure. This is especially prevalent in networking, since both areas use the same hardware for communications.
What we really need from a security standpoint, is a defense in depth approach. There are many different attack vectors into OT systems, and utilities need a multitude of security features to compensate. Entities need properly managed access points, segmented networks, controlled communications, secure remote capability, strict access controls, and properly patched systems. These security controls are also meant to work in tandem with efforts in physical security of OT systems as well.
From a physical security perspective, there has always been a long history of utilities dealing with thefts, vandalism, and sabotage at their facilities. One of the most common ways utilities are protecting their BES assets, is to physically separate the IT and OT networks. Using this approach will prevent any physical attacks from effecting both IT and OT assets. Even though this approach will reduce the ability to directly affect the Grid, there are numerous other secondary approaches one can take to disrupt operations. Employee information including any physical security credentials typically reside within IT networks. With that information, an individual can clone an ID card, or card access tag, and obtain access to critical assets and locations. This is one of the main reasons why security experts across the industry are suggesting that utilities begin to review their IT networks to see if the protection is adequate.
As with electronic security, within the physical security world, the more layers of security a utility has, the harder it is to penetrate the system. There are numerous ways to implement this defense in depth strategy; one of the most common ways is to separately lock critical assets, both IT and OT, within a separate locked room or cabinet. This will be supplemented by a locked building/gate entrance. FIGURE 1 as seen on the following page, you will find a rough sketch to see an example of a defense in depth strategy.
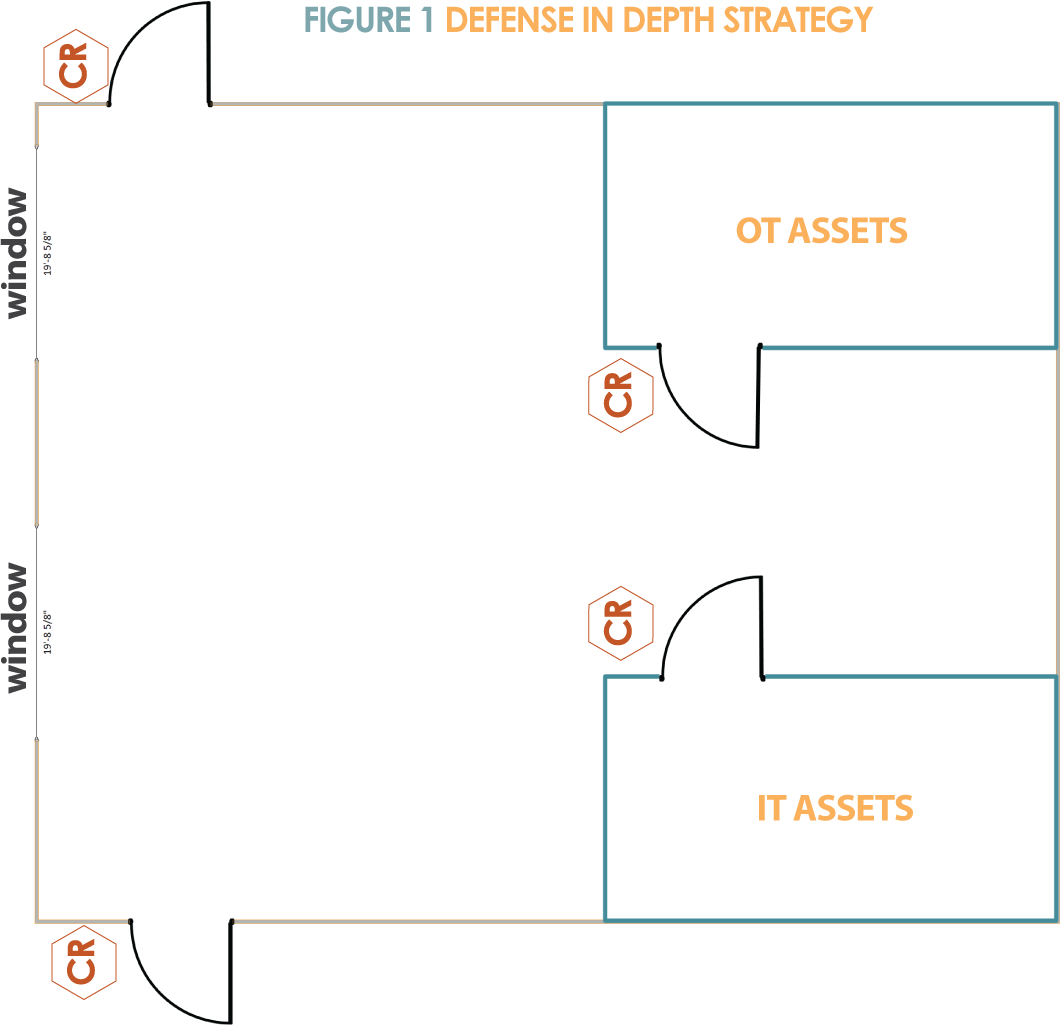
Within this example, there are card readers on each door that will only allow an individual with the correct permissions to access that room. Card readers (labeled CR in the diagram) are one aspect of the Physical Access Control System (PACS). The PACS can be setup to limit the individuals entering one room or area from another. This can allow a different area to have a more restricted access, than the previous area. The PACS can also be setup to allow door and glass contacts. This gives the utility the ability to monitor for any unauthorized access or alarms within the system. Another approach a utility can use, while still implementing a defense in depth strategy, is to key each room containing critical IT and OT assets separately. This way, an individual, with only access to the room, cannot enter an area or cabinet with IT and OT assets without proper authorization.
A third example is having a secured data center where both IT and OT assets reside. By limiting access to the data center to only key IT/OT personnel, that have received the training and passed a Personnel Risk Assessment (PRA), the entity can protect its cyber systems both through Human Resources and physical security protections. Having one secured data center works best in the situation where the Utility is using an IT/OT Team approach, and not differing security practices.
Within the NERC Standards, it is only required that BES facilities have a single form of physical security on their OT assets (with more stringent controls the higher an impact that facility or control has); however, it is always best practice for each utility to review their own physical security and determine if they are adequately protecting their IT and OT assets from any potential vandalism, theft, or sabotage.
In today’s environment, the difference between IT and OT systems are becoming less clear. Many OT systems now have similar characteristics of an IT system. Smaller electric utilities are many times faced with deciding what areas are better to staff and protect, their IT systems that contain critical customer data or OT systems that control the electric system. It is possible to do both utilizing the same set of resources that can help save cost, and result in a better security program for the electric utility.
This article focused on how the NERC Standards can be used for both protection of OT assets but also as best practices for protecting critical IT assets. The NERC CIP Standards are continuing to evolve to meet new challenges that electric utilities face in their OT environment and working together as a team of IT and OT experts can make the implementation of these new security standards more effective and efficient for a small to medium size electric utility.
Acknowledgements
This article is based on the paper “Securing the Grid and Your Critical Utility Functions” published in the 2017 IEEE Rural Electric Power Conference (REPC)proceedings and presented at the 2017 IEEE REPC Conference. © 2017 IEEE http://ieeexplore.ieee.org/document/7967006/
For more information or to comment on this article, please contact:
 Bill Bateman, Senior Project Manager | CONTACT
Bill Bateman, Senior Project Manager | CONTACT
GDS Associates, Inc. – Marietta, GA
770.425.8100
DOWNLOAD PDF
Also in this issue: Tax Cuts & Jobs act 2017 Impacts Formula and Stated Rates
GET OUR NEWSLETTER
RECENT POSTS
Archives
- December 2015 (8)
- January 2016 (6)
- July 2016 (6)
- March 2021 (6)
- May 2022 (6)
- August 2020 (5)
- March 2015 (4)
- January 2019 (4)
- June 2019 (4)
- August 2019 (4)
- February 2020 (4)
- May 2020 (4)
- June 2020 (4)
- December 2020 (4)
- July 2021 (4)
- October 2021 (4)
- April 2015 (3)
- August 2016 (3)
- February 2017 (3)
- July 2017 (3)
- February 2018 (3)
- February 2019 (3)
- November 2019 (3)
- March 2020 (3)
- April 2020 (3)
- September 2021 (3)
- December 2021 (3)
- August 2022 (3)
- December 2022 (3)
- April 2023 (3)
- July 2023 (3)
- December 2023 (3)
- May 2014 (2)
- February 2016 (2)
- March 2016 (2)
- September 2016 (2)
- November 2016 (2)
- January 2017 (2)
- July 2018 (2)
- November 2018 (2)
- March 2019 (2)
- May 2019 (2)
- July 2020 (2)
- September 2020 (2)
- April 2021 (2)
- August 2021 (2)
- February 2014 (1)
- April 2014 (1)
- July 2014 (1)
- August 2014 (1)
- November 2014 (1)
- February 2015 (1)
- May 2015 (1)
- June 2015 (1)
- November 2015 (1)
- October 2016 (1)
- December 2016 (1)
- October 2018 (1)
- December 2018 (1)
- April 2019 (1)
- July 2019 (1)
- September 2019 (1)
- October 2020 (1)
- November 2020 (1)
- February 2021 (1)
- April 2022 (1)
- July 2022 (1)
- October 2022 (1)
- August 2023 (1)
- October 2023 (1)
- April 2024 (1)
Categories
- News (78)
- Newsletter - TransActions (75)
- Employee Spotlight (35)
- Energy Use & Efficiency (27)
- Environment & Safety (10)
- Other Specialized Services (8)
- Transmission (7)
- Cyber Security (4)
- Energy Supply (4)
- Power Supply (4)
- Hi-Line: Utility Distribution Services (3)
- Uncategorized (2)
- Utility Rates (2)
- Agriculture (1)
- Hi-Line: Seminars & Testing (1)